How Can We Help?
GiniConnect Protocol
The GiniConnect Protocol was born from the important lessons that we learned developing, stress-testing and ultimately retiring the Gini Name System (GNS). This article briefly summarizes the reasons for this and the significant benefits of the GiniConnect Protocol. (For a much deeper technical understanding of GiniConnect and why it's so unique, please read GiniConnect Protocol: Trustless & Secure Communications.)
The holy grail of cryptocurrencies is a safe, secure and user-friendly mechanism to allow stakeholders to participate in a cryptocurrency ecosystem without having to interact with long, ugly crypto payment addresses like this:
gini_3zdco6d9mz8yu1u8s3p9pwj71u8hx3udxw9pfxtj4wtzr1gkraimj6utpqq7
(Yes, that's a real Gini public payment address that is valid on the live Gini Network right now, but don't send any money to it because that node is only for testing purposes!)
Long-form addresses work fine if you're not afraid of them and don't accidentally make a typo and send the payment to a wrong or non-existent address. But some people literally have a panic attack when they see long crypto addresses. In fact, we know that those scary addresses are one of the biggest reasons why cryptocurrencies haven't become more widely adopted. That's why Gini has been working diligently to solve this problem.
Mapping Email Addresses to Crypto Addresses is Not the Solution. There are several ways to solve the "scary crypto address" problem, but they are not equally safe and secure. One way is to map relatively simple, common account-based identifiers like email addresses, phone numbers or DNS records to a crypto payment address. This was the essence of the GNS: Whenever a stakeholder wanted somebody to send them Gini currency, they would say, "Just send it to my email address or phone number from your Gini payment screen!" This functionality was based on a mapping server architecture, which mapped the email/phone addresses to the GNS records that the stakeholders created from within their Gini GUI. It worked just like the mapping between numerical IP addresses and human-friendly website domain names in the Domain Name System (DNS).
We Hack Ourselves to Protect Stakeholder Security. In terms of user-friendliness, the GNS worked well and dramatically reduced the complexity of sending crypto payments. However, our continuous internal penetration testing and hacking our own systems revealed that no name resolution system is sufficiently secure for mapping payment addresses to email addresses, phone numbers, Facebook accounts or any other identification token/proxy unless a truly trustworthy mechanism is established that enables users to guarantee that their very first connection is with the correct party.
All Email & Phone Systems and Any Systems that Depend on Them Are Insecure. Many security researchers know that all public email and phone systems are fundamentally and fatally flawed from a security perspective. This means any system (including Facebook, Twitter, Gmail, Instagram, etc.) that depends on email/phone accounts is insecure, too. We hoped we would be able to overcome some of the problems that plague those systems by adding layers of encryption, anonymous biometric identification checks (under certain conditions), and other anonymous ID verification mechanisms based on zero-knowledge proofs. But piling on more security mechanisms is like piling on more layers of clothing to escape the cold: At a certain point, the entire system becomes so unwieldy and inflexible that it no longer functions according to the originally intended performance requirements.
A Truly Secure System Does Not Have Any Substantial Dependence on Insecure Channels. The more we tried to pile additional security mechanisms onto the fundamentally flawed and insecure email and phone systems, the more we realized it was a lost cause. This is a deep technical topic, but in summary, we concluded that the GNS can't have any substantial dependence on email, phone, DNS or any external name/account resolution system operating outside the secure Gini protocol suite because they're all relatively easy to hack and/or manipulate by a skilled and determined hacker or well-funded state actor.
Are You Connecting to the Correct Party? The principle of "connecting to the correct party" might seem simple conceptually: "Just get the unique phone number and email address from the parties and you're done!" some people might say. However, from a network security protocol perspective, it's a deep topic because there are many ways that a hacker/NSA/etc. can intercept insecure communications; hack email/phone accounts; impersonate you with those hacked accounts; socially engineer and bribe banks, crypto exchanges and corporate executives to give them your sensitive data from within their databases . . . if the system is not designed in a fundamentally secure, private and decentralized way.
No Profit Motive is Worth Risking Stakeholder Security. Unlike for-profit corporations that often sacrifice security to increase profit, our fundamental mission is to create the most secure, equitable, sustainable and user-friendly ecosystem for real-world commerce. Although the GNS was never hacked and the probability of a serious hack was relatively low, we were not willing to take any risk at all with our stakeholders' security.
What Does a Secure and User-Friendly System Look Like? After concluding that the GNS was not the optimal solution for the "scary crypto address" problem, we started thinking about creating a multi-channel protocol. Our goal for this protocol was to enable stakeholders to easily exchange contact records (including their Gini payment addresses) in such a way that they could guarantee the security of their initial payment address exchange and the authenticity of their counterparty without needing to see any long, scary crypto addresses. Additionally, our goal was to make the process as automated as possible while simultaneously eliminating all the common attack vectors.
Is a Trustworthy System Possible? The core question is: Is it possible to create a multi-channel user-authentication and connection protocol that is not dependent on any insecure channels, does not require stakeholders to reveal their personal identity to Gini, is fundamentally impervious to hackers and corruptible authorities, and does not impose tedious and time-consuming steps on stakeholders? In other words: Can we create a trustworthy and simple way for humans to connect in the Gini ecosystem? The answer is yes and it's called the GiniConnect Protocol. (See Why Trust Gini? to review the difference between "trustworthy" and "trusted" systems.)
The Solution: The GiniConnect Protocol. Based on the Gini Account Center software's simple contacts management feature, GiniConnect enables stakeholders to securely authenticate, connect and share their contact details and Gini payment address with another Gini stakeholder in less than 60 seconds. In some ways, GiniConnect works like the SWIFT banking system works from a bank manager's perspective, which is how banks securely communicate with other banks whenever they need to send wire transfers on your behalf. But in our case, GiniConnect essentially makes every Gini stakeholder the owner of their own personal SWIFT interface with a much more efficient, decentralized and user-friendly workflow.
The following screenshots illustrate how it works.
Contacts Screen:
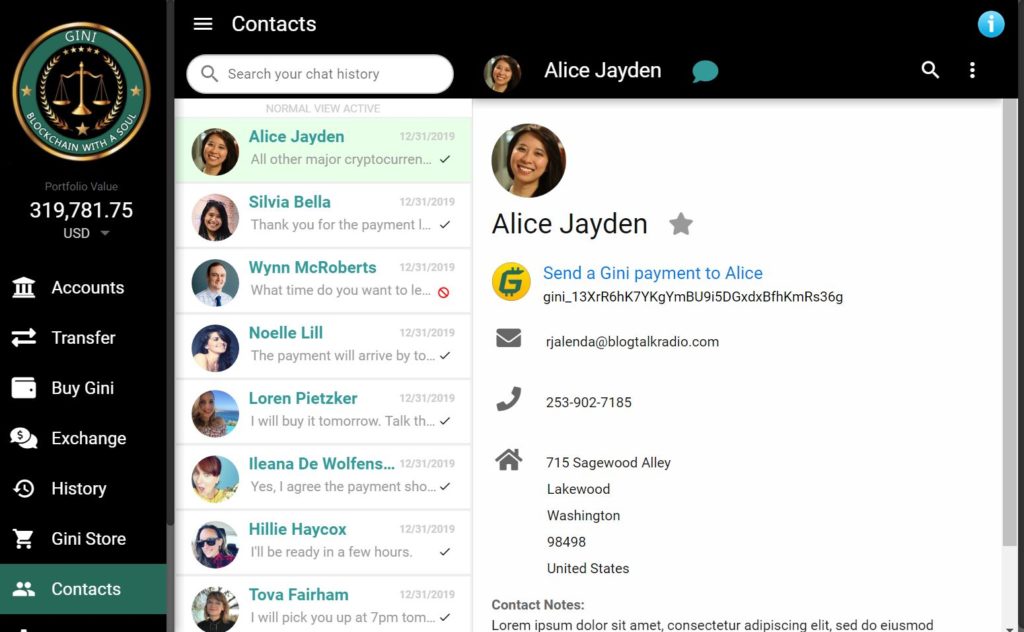
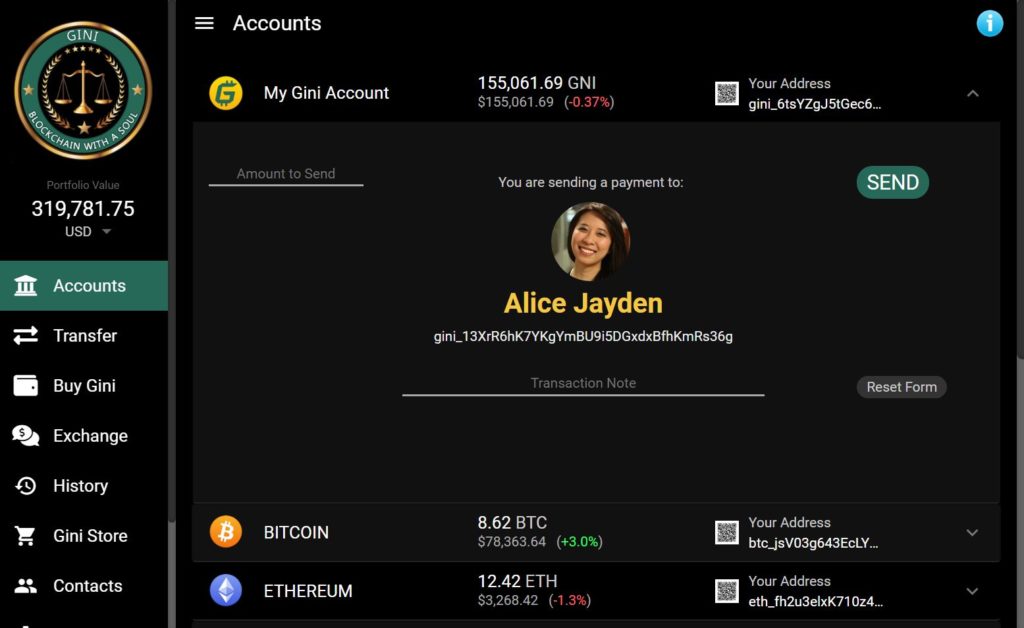
Usage Scenario: Alice and Bob know each other and want to exchange Gini contacts and payment addresses without having to touch any long crypto addresses. If they've already created a secure contact, they can simply click the Gini currency icon/link from the contact's profile to send the payment. That automatically loads the contact into the simple payment screen, as illustrated below.
If Alice and Bob haven't already established a secure GiniConnect connection, they would make their initial trustworthy connection by Alice clicking on "New Secure Contact" from the GUI, which is illustrated below.
![]()
Then there are only three simple steps to establish a secure GiniConnect connection.
Step 1: Create Gini Flash Code.
![]()
![]()
Step 2: Share Flash Code. Alice shares the Flash Code with Bob through an existing encrypted channel that she already trusts. This could be an encrypted voice or text chat using any of the popular encrypted chat programs like Signal, Telegram, WhatsApp or simply calling Bob to share the details over the phone. (Although, phones are less secure and we don't recommend it.) Even doing it by phone or encrypted voice chat is easy because the Flash Code is much shorter and easier to share than a random 64-character crypto address.
Step 3: Connect. Bob enters Alice's Flash Code by clicking on "New Secure Contact" from his own Gini Account Center GUI.
![]()
Alice instantly sees the connection request in her Account Center GUI, which she can accept or reject. In virtually all cases, Alice would accept the connection because spam is impossible in this context and she knows the counterparty is authentic for all the following reasons:
- Alice initiated the exchange.
- Alice easily generated the random Flash Code herself without depending on any insecure phone, email or third-party channels.
- The random Flash Code expires in 3 minutes, which is plenty of time to establish a secure connection with a truly trusted counterparty, but not enough time for a hacker to devise a successful attack. (The entire GiniConnect process typically takes less than 60 seconds.)
- When the Flash Code is transmitted over the network from Bob to Alice during the connection process, the Gini software encrypts the Flash Code into 160-bit random code (e.g.: 372ba72670b03c1f6a9d09eb5e1ce8f5933ff450), then transmits that encrypted payload over a bank-grade Secure Sockets Layer (SSL) connection, then automatically validates the payload on Alice's side to confirm that Bob has sent the correct cryptographically secure Flash Code. Computationally, it would require over 39 octillion years (3 quintillion years longer than the lifespan of the universe) to brute-force hack the 160-bit code, but hackers only have 3 minutes.
- No man-in-the-middle attack is possible.
- No centralized corporate cannibals or authorities can be compromised or coerced by corruptible politicians and corporate executives.
- No hijacked email accounts or insecure SMS codes to compromise the exchange.
- Even if somebody hacked Alice's email, phone or computer, they would never have a fresh random Flash Code with enough time to impersonate her.
The Simplest Payment System Humanly Possible. Alice and Bob's mutual contact details and Gini payment addresses are securely and automatically loaded into their respective Gini Account Center contact records without needing to see any long crypto addresses at all. Their contact information is not stored on any centralized server; so nobody (not even Gini) can see their details. From that moment forward, whenever Alice wants to send payments to Bob (and vice-versa), Alice can simply click on the "Send Payment" link on Bob's contact profile or start typing "Bob" into her Gini payment screen and Bob's name and payment address are automatically inserted into the recipient box. (The long payment address is also displayed in small font in case the sender wants to visually confirm it.) Nothing could be simpler.
Every Gini Stakeholder Has Their Own Personal SWIFT System. The Secure Gini Chat tool built into the Gini contact management GUI enables stakeholders to communicate securely and privately with all their trusted payment counterparties. (Clicking the blue-green icon next to the contact's name in the toolbar toggles between Chat Mode and Contact Details Mode.)
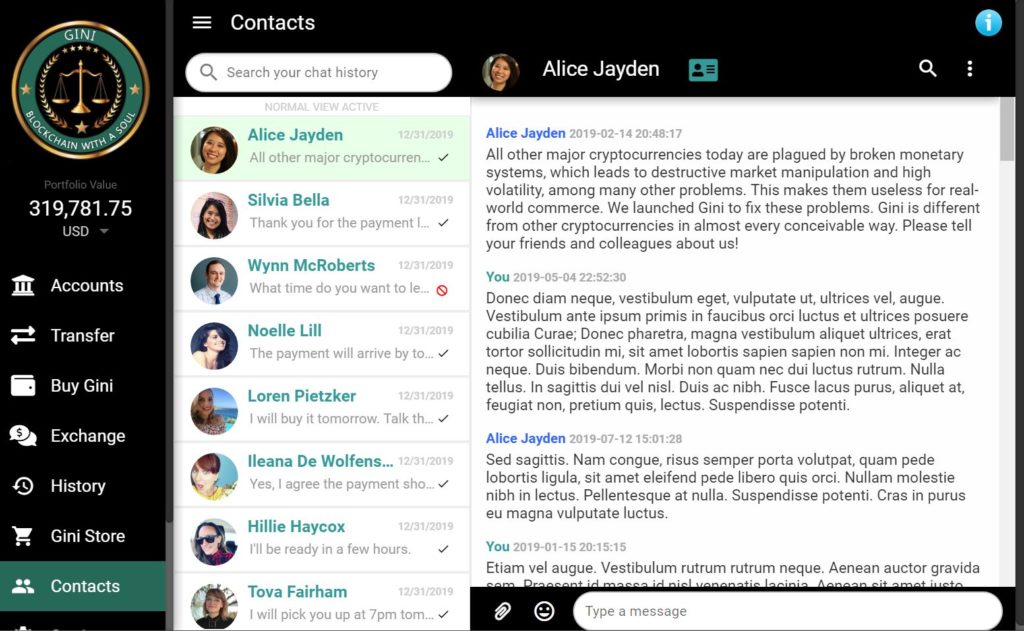
The chat tool enables stakeholders to keep all their private payment conversations organized with all their other private financial account data in the secure Gini Account Center software, just like fiat bankers do with SWIFT terminals. We're not big fans of the fiat banking system, but in this case, we're pretty enthusiastic about liberating Gini stakeholders from the toxic fiat banking system by empowering them with their own private, decentralized SWIFT system!
Conclusion. The GiniConnect Protocol eliminates typos and all the security risks associated with sharing sensitive financial details via insecure channels. Billions of people already know and use encrypted chat tools like Signal, Telegram and WhatsApp every day. Now they can use Secure Gini Chat to manage their own private SWIFT systems within the unique, equitable and sustainable Gini ecosystem. Eventually, we hope the Secure Gini Chat component will also become a popular communications tool beyond our current use case, but for now, it works well for Gini stakeholders who want to securely connect and communicate in real-time with their trusted payment counterparties.
Note: To prevent stalkers and other malefactors from harassing the Gini staff and engineers, the contact phone numbers, email addresses and other personal information displayed on this page are randomly generated for illustrative purposes only. We do not know if any actual people own those numbers and addresses.
Did You Like This Resource?
Gini is doing important work that no other organization is willing or able to do. Please support us by joining the Gini Newsletter below to be alerted about important Gini news and events and follow Gini on Twitter.

