How Can We Help?
The Gini Trust Protocol
This article complements the Why Trust Gini? article to provide a more technical exploration of the concept of trusted systems and the Gini Trust Protocol in particular.
Visualizing the Gini Trust Protocol
Before we dive into the details, it usually helps to visualize what we are talking about first. Below is an animation that illustrates how consensus is achieved between nodes on the Gini Network.
Now let's dive into the details.
The Byzantine Problem. There are many ways that bad actors can try to manipulate a decentralized ledger, but most attacks are based on trying to inject inaccurate information into the ledger. In Computer Science, this is often classified as the “Byzantine Generals Problem.”[1] In summary, this means that bad actors may have incentives to manipulate the flow of information between nodes to corrupt the state of the ledger for self-serving reasons. Malfunctioning nodes can also create byzantine conditions.
The Purpose of a Consensus Protocol. No matter how byzantine attacks occur, the problem requires us to ask two basic questions: Who is allowed to build the ledger? How do we achieve consensus about what goes into the ledger? Answer: We employ a systematic consensus protocol that enables the system to automatically and impartially select trustworthy (not trusted) nodes, which will also allow those trustworthy nodes to achieve consensus about the current state of the ledger.
The Religion of “Trust-less” Blockchains. In the beginning of every crypto-fan’s journey into the world of decentralized systems, we are introduced to the concept of “trust-less” systems. The concept of building a system that doesn’t depend exclusively on trust in any particular human or entity is crucial to building high-integrity systems and institutions. However, the puritanical ideology at the heart of the crypto world today has transformed this concept into a veritable religion. The mantra of this religion is “trust nothing.” It’s an inspiring mantra for those of us who are sick of seeing our economic and political systems destroyed by supposedly trusted corporations and politicians, but the people who embrace this mantra often ignore many technical realities associated with how scalable, decentralized systems work in the real world.
Decentralization in the Real World. Anybody can read a dictionary or textbook to memorize the academic definition of “decentralized,” but in the real world, things are much more complicated. To understand why the puritanical “trust nothing” religion is problematic, we need to understand a few core principles about system design in the real world.
- The concepts of “trustworthiness” and “trusted” are not synonymous.
- Something that is trusted for a short period of time doesn’t mean it must be trusted forever.
- A system without a way to allow stakeholders (humans or non-human nodes) to earn certain levels of trust will never be truly decentralized because it will never be truly scalable. Why? Because the system’s administrators will never be able to effectively perform all the work required to maintain any large, decentralized system without being able to delegate certain activities to trustworthy ecosystem participants. Without meaningful, broad-based delegation to dynamically trustworthy ecosystem participants, the system will inevitably become highly concentrated like the crypto and fiat markets are today. Thus . . .
- Trustworthy delegation is the most important principle in building any scalable and sustainable decentralized system.
Effective Delegation is Based on a Continuum of Trust, Not Binary Decisions. Binary decision-making is intoxicating because it seems to reduce the complex universe of choices to simple all-or-nothing, black-or-white, on-or-off, right-or-wrong decisions. We know from first-hand experience that many software programmers, engineers, and mathematicians get frustrated when unpredictable human nature craps all over their rationally designed models and systems.
The Real World is Not Binary. Unfortunately, the real world of sociology, economics, and geopolitics rarely conforms to binary logic. The real world is usually messy and requires much more nuance than any binary decision tree can handle. Thus, anything at the intersection of human nature, economics, and geopolitics (e.g., cryptocurrencies) can never be based on a “trust nothing” ideology. In the real world, every system operates based on a continuum of trust, not a “trust or don’t trust” binary decision. In the Gini technical documentation, we call this principle a "decentralized continuum of ephemeral trust".
The Gini Trust Protocol. The concept of a “consensus protocol” implies trust in the system that facilitates consensus; and that trust must be based on something. This is another reason why the “trust nothing” religion is not realistic from the perspective of anybody who has real-world experience in business, geopolitics, or complex human-system interface design. In reality, a “consensus protocol” alone is not enough; blockchain teams need to adopt a continuum of trust if they want to build scalable, sustainable, decentralized systems. For this reason, and to reflect the reality of the real world, we call the Gini BlockGrid protocol the “Gini Trust Protocol,” not merely a “consensus protocol.”
What's Wrong With Existing Consensus Protocols?
Proof-of-Work Consensus Protocols. Pure Proof-of-Work (PoW) is the most commonly used consensus protocol in cryptocurrencies today. However, PoW-based blockchains are unsustainable because PoW unnecessarily wastes electricity and incentivizes users to waste money on expensive computing hardware and services. If Bitcoin were a country, it would be in the top-50 highest energy-consuming countries on Earth (#43 in the chart below) . . . and Bitcoinistan’s energy consumption continues to grow rapidly.
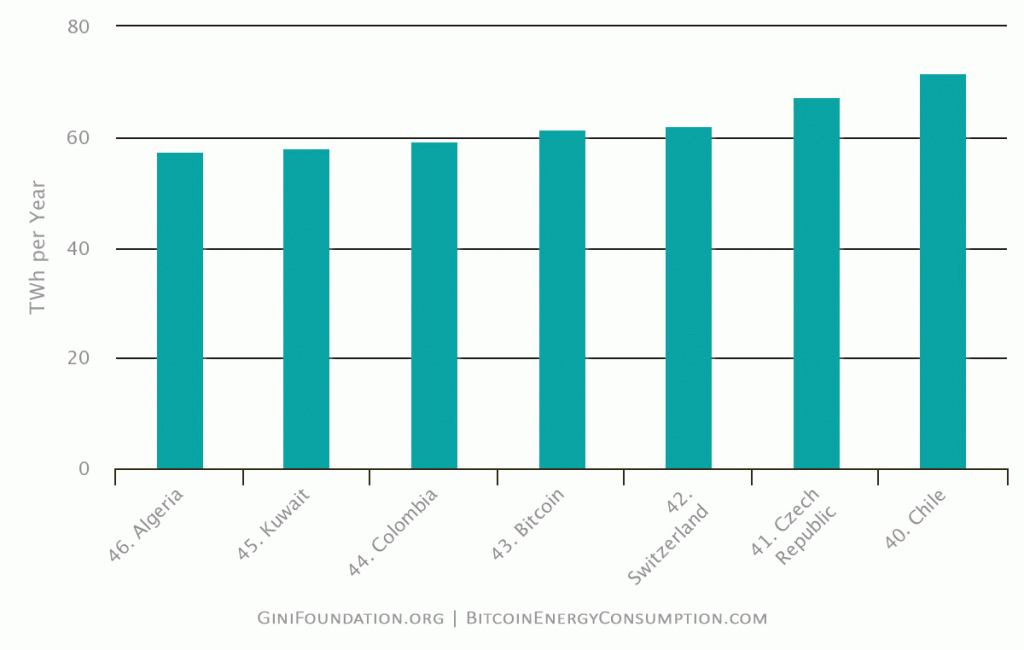
USD Billions of Wasted Resources. The chart above does not include the energy consumption associated with manufacturing USD billions worth of Bitcoin mining equipment or the energy consumption and equipment manufacturing associated with all other PoW-based blockchains. These expenses and byproducts waste finite natural resources and add no human value to the world beyond the profits they produce for a tiny number of companies; and those profits are primarily consumed by an even smaller number of the largest shareholders in those companies.
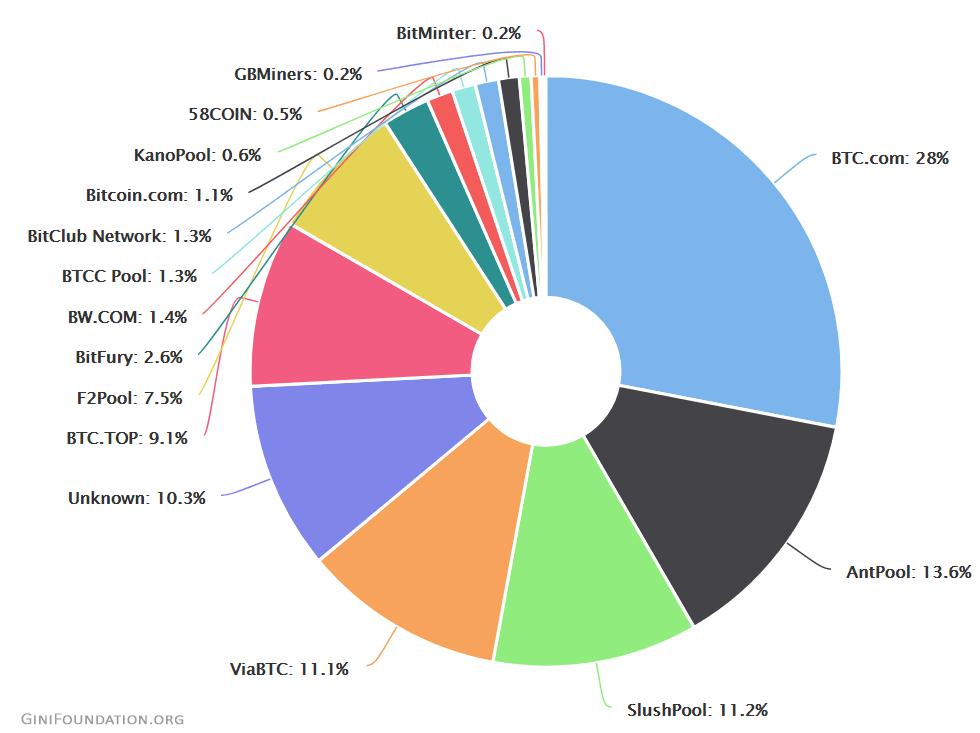
Techno-Oligarchies. PoW-based blockchains typically result in a technological arms race in which the wealthiest and most technologically savvy entities are able to purchase the most powerful mining equipment. This inevitably creates a techno-oligarchy that substantially dominates the entire ecosystem, which can be clearly seen in the chart below. In the chart, only five entities control nearly 75% of the entire Bitcoin network; and only seven entities control 91% of the Bitcoin network. For anybody who truly cares about decentralization, this is intolerable; and there’s no rational reason to believe the oligarchy will voluntarily distribute their wealth and power throughout the Bitcoin ecosystem anytime soon. (And no, trickle-down economics won't help.)
Proof-of-Stake Consensus Protocols. As we observed in the charts and cryptocurrency community debates presented in the Gini book, pure PoS-based blockchains inevitably lead to high concentrations of wealth and power by rewarding whales simply for being whales. Advocates of pure PoS often embrace a puritanical form of libertarian ideology that can be boiled down to this: “Investors who risk their money should be given the most power. Whoever doesn’t like it can sell their coins and leave. . . .” (That’s a quote from somebody I debated in another cryptocurrency community.) If only human civilization, economics, and geopolitics were that simple.
What’s the Point of Crypto Economies if They’re More Concentrated than Fiat Economies? Both pure PoW and pure PoS lead to perpetual cryptocurrency oligarchies just like humanity suffers from in the fiat world. This creates a perpetual cat-and-mouse game with whales and mining pools who inevitably use their power to prioritize their own interests above the interests of the broader ecosystem. This has profoundly negative consequences on any crypto or fiat ecosystem’s long-term development and governance.
More Complexity Does Not Fix the Problem. Many crypto teams think they can fix their problems by creating ever-more complex systems. For example, the Bitcoin community is trying to reduce their high transaction fees with new approaches like the "Lightning Network." However, even if they could reduce the transaction fees, they will never be able to eliminate all the other problems because Bitcoin is already dominated by a tiny number of powerful special interest groups, just like the fiat-based economic and political systems are today. In other words, complexity doesn’t change the fundamental reality: Any crypto or fiat ecosystem that is not . . .(1) launched on a solid monetary system foundation of broadly distributed wealth and power; and
(2) built with proactive and automated ecosystem sustainability mechanisms that ensure the broad and sustainable long-term creation and distribution of wealth and power;. . . will never escape the trap of concentrated wealth and power without a violent revolution.
Crypto-Oligarchies Lead to Revolutions Just Like Fiat Oligarchies. Violent revolutions have occurred frequently in human history in response to high concentrations of wealth and power in the fiat world. In cryptocurrency projects, “violent revolution” means the community and software code forks into two or more communities and code repositories, which often do not survive the divorce. Gini is the result of a philosophical revolution against the puritanical libertarian ideology that dominates virtually every cryptocurrency project on Earth today. (Recall every member of the Gini team was previously a libertarian; so, we’ve seen the world from both perspectives. See the Gini School of Economics Introduction for more context.)
Technical Factors
The Gini “Ledger”. Before we continue, it’s important to understand what we mean by “ledger” and the distinction between a “public global ledger” and a “private account ledger.” Given Gini’s BlockGrid architecture, the “Gini ledger” has a substantially different meaning than it does in other legacy cryptocurrencies. We usually use the term “ledger” as a simple shorthand, but technically, each Gini stakeholder has their own private account blockchain, which is siloed and anonymously linked to the broader Gini BlockGrid (aka the global ledger). This grid-based architecture enables all Gini nodes to verify the validity of any transaction and the integrity of the global money supply at any time.
Only randomly selected, authorized Guardian nodes (defined below) can validate transactions on the global public ledger, which provides a single source of truth for the entire network. In contrast, at the “private account ledger” level, only a stakeholder’s own node can add transactions to its own ledger based on the funds sent/received between direct stakeholder accounts.[2] This architecture eliminates entire categories of security threats and makes ledger-forking (a daily occurrence in Bitcoin and virtually all other cryptocurrencies) nearly impossible on the Gini Network.
Thus, in Gini’s context, the concept of “consensus” is primarily about which nodes have the authority to validate exceptional transactions (i.e., ledger forks) on the public global ledger. This is the meaning of “public ledger” from this point forward.
Examples of How the Gini Trust Protocol Works. To understand and appreciate why the Gini Trust Protocol can achieve a much greater level of real-world decentralization, speed, and scalability compared to other cryptocurrencies, it’s useful to consider a few examples of how the Gini Trust Protocol works. As you read, please keep in mind that any one of these features by itself might theoretically be defeated under some imaginary set of hostile conditions. However, the protocol is based on a multi-factor trust analysis engine (the “Gini Trust Engine” or “GTE”), which is predicated on the principle that trust is a continuum, not a binary decision. In this context, one trust factor alone might seem relatively simple to defeat, but collectively, they are impossible for an attacker to overcome under real-world conditions.[3]
Dynamic Guardian Nodes
- Randomly Selected Dynamic Guardians. The Gini Trust Protocol randomly selects nodes throughout the network based on a lottery algorithm that is continuously running. When a node wins this lottery, it temporarily becomes a Dynamic Guardian node. (The purpose of a Guardian node is similar to a Bitcoin miner node, but much faster and without the techno-oligarchy.) Many Guardian nodes can operate and validate transactions in parallel, which results in dramatic speed improvements compared to other blockchains.
- Random Guardian Sessions. Guardians are authorized to validate transactions for the Gini public ledger for a random, limited duration of time, which is called a “Guardian Session.” Random Guardian Sessions start when the node wins a lottery and each session can last for several minutes or hours. A Guardian has the privilege of updating the public ledger only during this narrow window of time.
- Only Guardians Can Update the Public Ledger. Bitcoin and other blockchains can fail if 33—51% of their mining hash power colludes and hijacks their public ledger. This kind of attack on Bitcoin is easy today because 91% of Bitcoin mining hash power is controlled by only seven entities; and all other major cryptocurrencies today suffer from the same concentration of wealth and network power. In contrast, no group of two or more attackers could ever effectively collude and hijack the Gini public ledger because the probability of them all becoming a Dynamic Guardian node at the same time is astronomically low. (See calculations below.) This makes a “51% attack” and Sybil attacks impossible under real-world conditions.
- Large Dynamic Guardian Pool Size. The pool of random Dynamic Guardian nodes is several hundred to 1,000 nodes at any given moment, but the pool of eligible Guardian nodes participating in the random lottery is unlimited. The unlimited pool of eligible Guardians ensures that the actual quorum of Guardians participating in the PoC at any given moment is sufficiently large to make it practically impossible for any significant percentage of total Guardian nodes to coordinate a successful malicious attack under real-world conditions.
- Defense Against Bot Army Attacks. Even if a sophisticated attacker developed an automated bot army to scan their private network, wait for increased node activity to detect a random Guardian Session on a node they control, and then attacked the Gini network with that one random Guardian node, they still would only be one Guardian node on the network—far less than the 51% of Guardian nodes required to compromise the integrity of the Gini public ledger. Thus, they would have no meaningful chance to successfully attack the Gini public ledger.
- Broad Geographical Distribution. The pool of Dynamic Guardians is distributed across a large geographical area, i.e., we will not launch the Gini MainNet until there are Dynamic Guardians operating in at least 20% of all countries and 40% of OECD countries. This reduces the cultural, political, and sociological links that would facilitate collusion, thereby making it even harder for more than 50% of Guardian nodes to coordinate an attack.
- Dynamic Guardians Must Prove Their Commitment to the Gini Ecosystem. The pool of Dynamic Guardians is based on Gini’s unique Dynamic Proof-of-Commitment (DPoC) algorithm, which is a key component of Gini’s Trust Protocol. DPoC grants Guardian status only to nodes that are probabilistically very likely to behave honestly.
Dynamic Proof-of-Commitment
Rewarding Commitment is the Key to a Sustainable Ecosystem. To ensure effective delegation and ecosystem stability, various privileges are granted to stakeholders in the Gini ecosystem who have earned them by proving their commitment to the ecosystem. Privileges are automatically granted based on several automated metrics, which eliminates the potential for individual bias, prejudice, or favoritism in the evaluation process.
Earning Privileges and Power in the Gini Ecosystem. A logical outcome of Gini's emphasis on Humanism over puritanical Libertarianism is the way stakeholders in the Gini ecosystem are defined, evaluated, and granted certain privileges. “Privileges” are things like voting power regarding technical development and ecosystem governance issues; periodic financial rewards for running Dynamic Guardian Nodes that contribute to the stability and integrity of the Gini Network; more powerful trading capabilities on the Gini Exchange; among others. Privileges are not rights; they are earned rewards intended to gradually and automatically decentralize the financial and political power throughout the Gini ecosystem.
Quantifying Commitment. A “commitment” can manifest in many ways and we strive to systematically quantify as many forms of commitment as possible. Measuring and rewarding commitment is a scalable and elegant solution to many of the problems that plague other cryptocurrencies today. In fact, measuring and rewarding commitment is the basis for many automated decision-making processes that occur throughout the Gini Platform’s technical development and ecosystem governance.
Guardian Selection Criteria
The Gini Trust Protocol is substantially based on Gini’s unique Dynamic Proof-of-Commitment (DPoC) algorithm, which automatically and dynamically selects and rewards high-quality Gini accounts/nodes and gives them Dynamic Guardian status on the network. Being a Dynamic Guardian is the highest and most rewarding privilege in the Gini ecosystem. Thus, there are strict requirements to be eligible for Guardian status.
Guardian Points System. Guardian status must be earned and automatically and continuously verified based on fulfilling all of the following minimum criteria (the "Guardian Requirements"). Each of these Guardian Requirements also corresponds with a certain amount of points. The more points a Guardian node has, the more weight it has during any protocol-level voting process (e.g., for Gini's automated consensus process).
- Account Age. The account must be at least 30 days old. This prevents many types of pump-and-dump scams and other malicious behavior.
- Points: 0-1,000.
- Minimum Stake Amount. The account’s Gini stake must be in the top-50% of all Gini stakeholders on the network. This is a low enough threshold to be egalitarian and inclusive of 50% of all stakeholders while also being high enough to confirm that an account has a meaningful stake in the Gini ecosystem. Stakeholders with a meaningful stake in the ecosystem are much less likely to abuse or manipulate the ecosystem.
- Points: 0-1,000.
- Minimum Stake Hold-Time. The account’s Minimum Gini Stake Amount must have been held for a minimum of 60 days prior to the then-current date-time. This discourages pump-and-dump schemes and many other kinds of market and protocol manipulation.
- Points: 0-1,000.
- Minimum Node Up-Time. The account’s node must have been connected to the Gini Network for a minimum of 95% of the minutes during the preceding 30-day period. Each minute, the Gini protocol pings Guardian nodes to confirm that they’re still alive and eligible for Guardian status. If a Guardian node is unresponsive for 3 consecutive pings (3 minutes), then the “down-time counter” begins and continues counting the node’s down-time minutes until the node is responsive again. If the node falls below the minimum 95% up-time threshold, then it is automatically removed from the Dynamic Guardian eligibility list until it comes back into compliance with the 95% threshold.
- Points: 0-1,000.
- Maximum Ping Response Time. The account’s node must have a maximum ping response time no greater than 100 milliseconds. This is an above-average response time for most intercontinental ping requests, which means this is an egalitarian and inclusive threshold, but it’s still fast enough to ensure that the account’s node is sufficiently responsive to serve as a Dynamic Guardian for the network.
- Points: 0-1,000.
- Minimum Bandwidth. The account’s node must have an average periodically tested download speed of at least 10 megabits per second, which was the approximate worldwide average speed in 2017. This is an inclusive threshold while still ensuring that the node's Internet connection is fast enough to efficiently serve as a Dynamic Guardian for the network.
- Points: 0-1,000.
- No Market Manipulation. Accounts that engage in blatant market manipulation, including pump-and-dump trading, bear raid trading patterns, attempts to execute fraudulent transactions, attempts to thwart any of Gini’s ecosystem stability mechanisms . . . are not eligible for Dynamic Guardian status. However, some activities (e.g., penetration testing and other automated activities) can do harm while also doing some good; so, there is a "Bad Actor Metric" that gradually reduces the node's points in this category over time to give stakeholders plenty of warning before their accounts become completely ineligible for Guardian status.
- Points: 0-1,000 Deduction: Based on a Bad Actor Metric, each bad action reduces points.
Robots Are Not Equal to Humans. Accounts that engage in high-frequency trading or any other rapid network activity that no human could ever perform are automatically disqualified from being Dynamic Guardians. The Gini ecosystem is intended to serve real humans, not robots. Robots create unpredictable network congestion, destabilizing market volatility, and do not add meaningful human value to human markets; so, they are generally discouraged on the Gini Network.[5]
Quantifying Gini Network Resilience
The following probability calculations illustrate how resilient the Gini Trust Protocol is to 51% attacks and various types of Sybil attacks.

Preventing the Double-Spend Problem. Imagine you purchased a computer for $1,000 and then grabbed that money back from the merchant and spent it again to buy a $1,000 bicycle. That would be unethical and illegal. This is called the “double-spend” problem. Because every decentralized ledger is updated asynchronously across all the nodes in the network, it can take a few seconds or minutes (if the network is congested) for all the transactions to sync across the network. These small sync delays could enable bad actors to rapidly execute double-spend transactions. So, Gini prevents this problem in two ways:
- Gini's BlockGrid architecture is inherently impervious to the double-spend problem because each stakeholder has their own private account blockchain. Thus, the impact of all transaction-level attacks (e.g., forks, double-spend attacks, and all types of transaction fraud) is automatically isolated to only the stakeholder account(s) involved in a particular transaction; thus, all other stakeholders are not impacted. In fact, the integrity of Gini's public ledger and corresponding Gini money supply is based on a cryptographically hashed chain of ending private ledger account balances, not a chain of individual transactions. This works because each ending account balance is merely the mathematical sum of x number of transactions; so, at the macro public ledger and money supply level, it's not necessary for the Gini Trust Protocol to analyze every single transaction if the protocol only needs to anonymously verify the chain of ending account balances to implicitly verify the integrity of all transactions. This is why Gini's account balance-based approach is much more efficient and private compared to the UTXO-based approach used by Bitcoin and most other cryptocurrencies today.
During a Network Attack, Gini Prioritizes Consistency Over Instant Availability. In Computer Science, there is a principle called the CAP Theorem, which states that during a network attack (e.g., a DDoS attack) it’s technically impossible for a distributed system to simultaneously provide more than two out of three guarantees: consistency, availability, and partition tolerance. Because financial transactions often include many dependencies on other transactions, trying to process transactions in real-time that are being disrupted by a large-scale attack could result in a cascade of out-of-sync data, which can then be exploited in various ways by bad actors.
Thus, consistency and partition tolerance are Gini’s highest priorities. That means, in the hypothetical case when Gini is under a network attack, the Dynamic Guardian nodes stop validating transactions (i.e., they reduce service availability) and they alert all other nodes that no more transactions will be processed until the attack is over. Prioritizing consistency and partition tolerance over availability is the only way to guarantee that stakeholder funds are protected during a network attack.
In Summary: The Gini Trust Protocol, Dynamic Proof-of-Commitment, Dynamic Guardian nodes, and the Gini BlockGrid architecture are all unique and important innovations that enable Gini to achieve true transaction privacy without significantly impacting transaction speed. These features also enable Gini to achieve strong public and private ledger integrity, which automatically results in strong macro money supply integrity. Collectively, we believe these features are compelling reasons to participate in the Gini ecosystem.
Notes:
[1] This is a deep field of study, which you can learn more about here: https://en.wikipedia.org/wiki/Byzantine_fault_tolerance#Byzantine_Generals'_Problem
[2] This unique architecture is how Gini achieves true transaction privacy, strong public and private ledger integrity, and strong macro money supply integrity.
[3] In Probability Theory, we are taught that nothing is impossible (Even the Earth exploding into a giant ball of pink cotton candy is mathematically possible.); so, to avoid offending any professors, we say it’s impossible under real-world conditions.
[5] If a stakeholder has an idea about an automated activity that they believe would be beneficial for the ecosystem (excluding the thoroughly debunked “HFT provides market liquidity” argument), then feel free to contact us to discuss how it can be implemented safely without adversely impacting the ecosystem.
Did You Like This Resource?
Gini is doing important work that no other organization is willing or able to do. Please support us by joining the Gini Newsletter below to be alerted about important Gini news and events and follow Gini on Twitter.
[mailpoet_form id="1"]

